5 Real Phishing Email Examples to Watch Out For (and How to Spot Them)
Most businesses have the basics covered when it comes to cybersecurity — firewalls, antivirus software, secure networks. But even with all that in place, the biggest risk usually isn’t your technology. It’s your people.
Phishing is one of the most common (and effective) tactics cybercriminals use to break in. These scams are designed to look legit and catch your team off guard — and they’re getting harder to spot.
At IT TechPros, we’ve been in this business for over 20 years; we’ve seen how fast one bad click can change everything. That’s why we believe that every team, no matter the size, should know how phishing works, what it looks like, how to avoid it, and what to do if someone takes the bait.
What is Phishing?
Phishing is a cyberattack where someone impersonates a trusted source — like a coworker, bank, vendor, or government agency — to get you to share sensitive information, download malware, or perform a costly action.
These attacks typically arrive in the form of:
Emails
Text messages
Phone calls
Fake websites
Download links
Phishing relies on social engineering (the act of manipulating human emotions like urgency, fear, or curiosity) to bypass logic and make people act quickly.
Why is Phishing So Dangerous?
Because it works.
Phishing doesn’t require sophisticated code or deep technical skills. It only needs one person to trust the wrong message. And once an attacker gains access, they can move through your systems, steal credentials, lock files for ransom, or impersonate internal employees to scam others.
Here’s why phishing is such a serious issue:
90% of data breaches begin with a phishing email.
The average cost of a phishing attack for a small business is over $100,000.
Phishing emails today often use real logos, cloned websites, and even previous email threads to appear legitimate.
No matter how strong your tech stack is, your employees are still the #1 target.
Phishing Examples
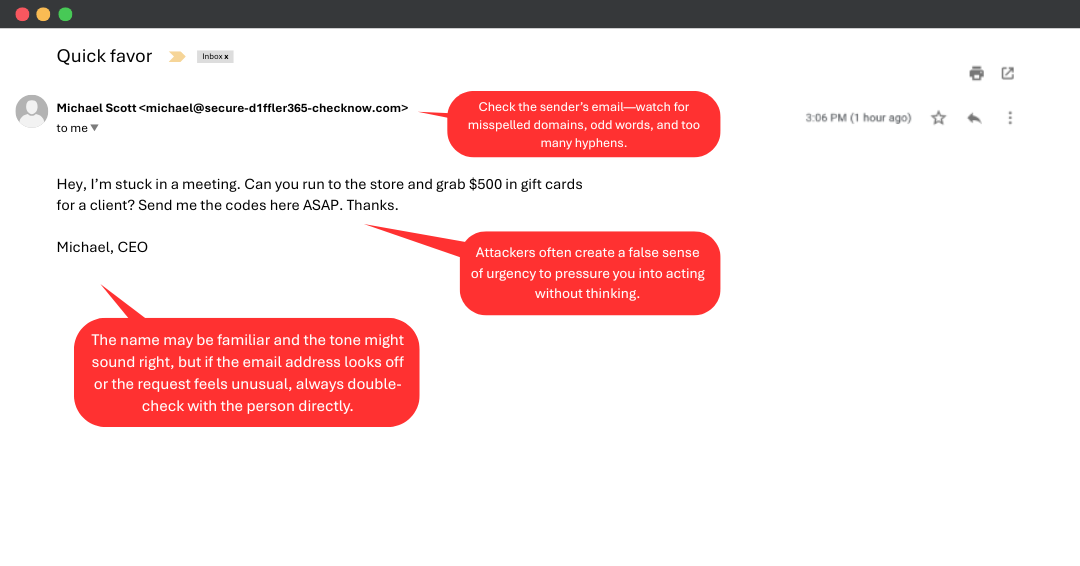
The “CEO Request” Scam
You receive an urgent email that appears to be from your CEO.
“Hey, I’m stuck in a meeting. Can you run to the store and grab $500 in gift cards for a client? Send the codes here ASAP. Thanks. -Michael”
Seems straightforward—but did this really come from your CEO?
Scammers often impersonate leadership and create urgency to pressure you into acting fast without verifying the request. Here’s what to watch for:
Unpersonal or generic greetings (or no greeting at all)
An unfamiliar email address that looks slightly off
A sense of urgency, pushing you to act fast without questioning
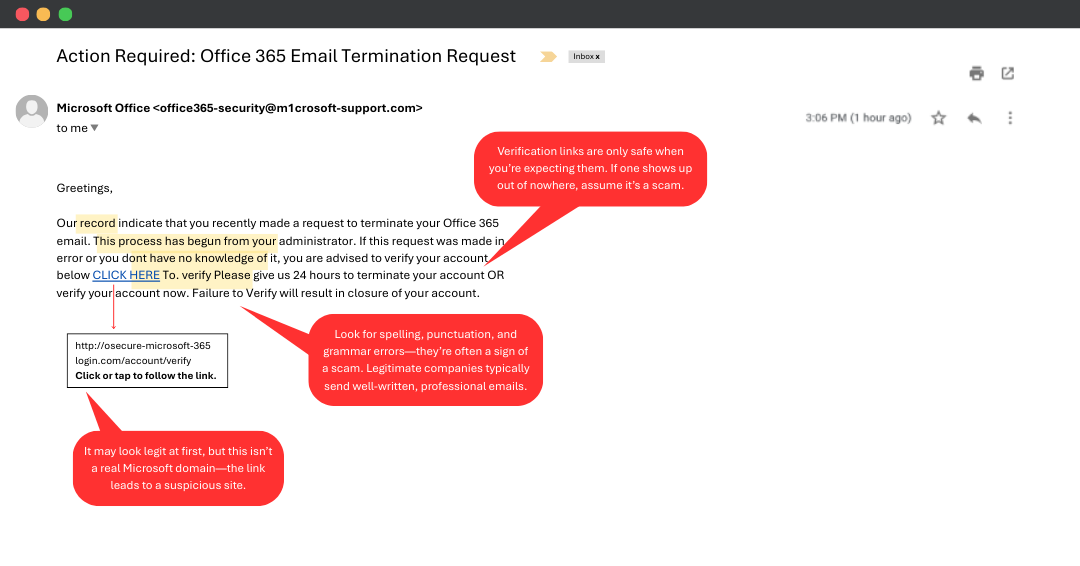
2. The Fake Account Verification Email
You receive an alarming message that says your account will be shut down unless you verify it right away. It looks official—logos, formatting, even a convincing tone. But the link takes you to a fake site built to steal your login details.
Here’s what to what to watch for:
A domain that’s slightly off (e.g.
@m1crosoft-support.com)Generic greetings or vague threats
Links asking for sensitive info when you didn’t request anything
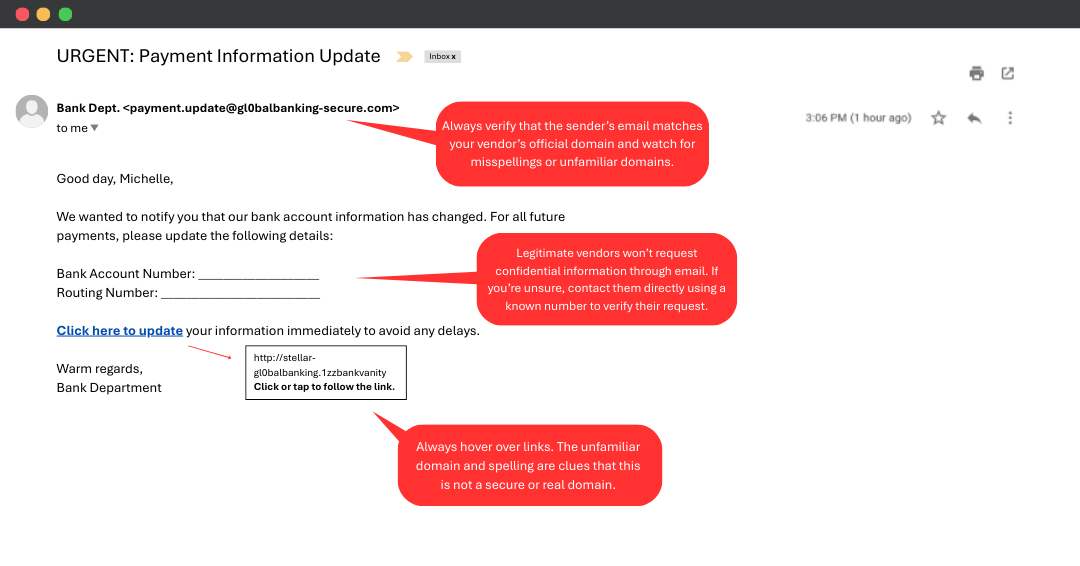
3. The Vendor Payment Scam
You get an email from what looks like a trusted vendor—your bank. It has the same logo and looks legit but it’s not really your vendor. It’s a scammer who’s spoofed their email and inserted themselves into your workflow.
These types of attacks are especially dangerous because they’re highly targeted and personalized. This type of phishing attack of called spear phishing.
Spear phishing: A fraudulent email that pretends to be from a legitimate source, like a bank, to trick you into revealing sensitive information or clicking on malicious links. It’s also a form of social engineering where attackers use deception to steal your personal or financial data.
4. The HR/Payroll Update Scam
You receive an email claiming your direct deposit details need to be updated. The email asks you to log in through a provided link.
At first glance, it may look like a legitimate message from your HR or payroll department, when in reality, it's a classic phishing attempt. If (or when) you enter your information, it will go straight to cybercriminals, who can then reroute your paycheck. These attackers pose as internal departments to deceive you into sharing sensitive information—such as your W-2, Social Security number, or login credentials—which they can then use to access your accounts or launch further attacks.
Remember, HR usually doesn’t ask for sensitive information via email or through third-party links. These changes should only be done through your secure and trusted HR portal or in-person.
Here’s what to watch out for:
Unsolicited requests for sensitive information like your banking information, W-2 form, Social Security number, or login credentials.
Lack of personalization. Legitimate HR emails usually include your full name, department, and specific job details.
Be skeptical of links or attachments asking you to update personal or payroll information. Always hover over links to see the true destination.
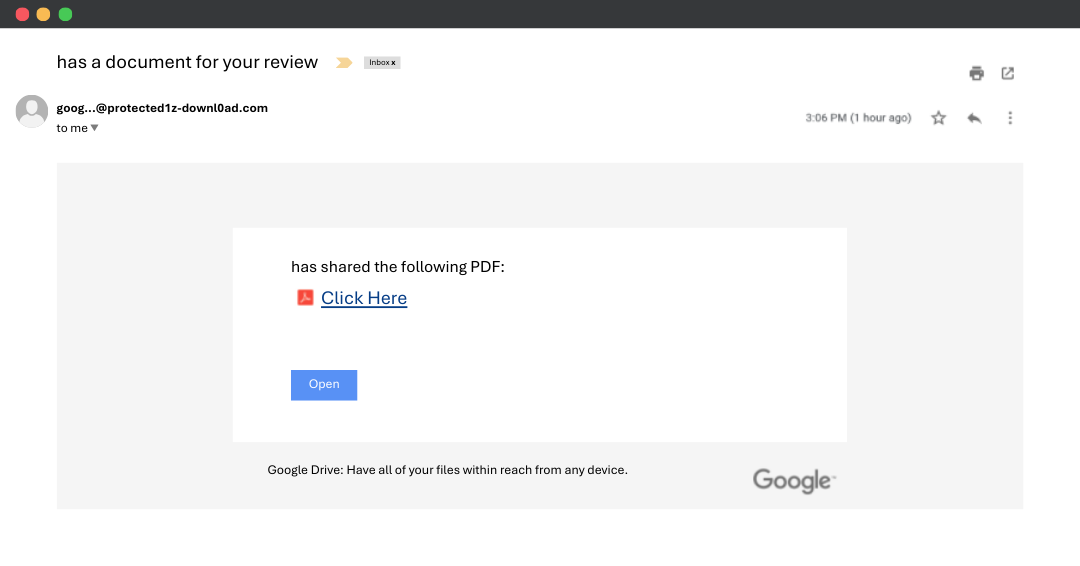
5. The “Your Document Is Ready” Scam
Not all phishing attacks happen over email alone. In a Download Link phishing scam, the attacker sends what looks like a trustworthy link from platforms like Google Drive, Adobe Sign, or Dropbox. The message may say something like:
“Your document is ready for review. Please download and sign ASAP.”
Once clicked, the link either:
Starts downloading malware onto the user's device.
Redirects to a fake login page to steal credentials.
Executes hidden code that gives the attacker remote access.
Here’s how to protect yourself:
Never download files from unfamiliar senders, even if the platform looks familiar.
Hover over links to preview the full URL before clicking.
When in doubt, verify the request with the sender through a different communication channel.
What Happens If You Click on a Phishing Email
Phishing attacks aren’t just annoying—they can be dangerous. Depending on the scam, you might:
Give away your credentials: Clicking a link and logging in can hand your username and password directly to attackers, giving them access to your personal or company accounts.
Send money to a scammer: Fake invoices or urgent payment requests can trick you into wiring funds that are impossible to recover.
Download malware: Clicking on links or attachments might install spyware or ransomware that compromises your device or network.
Expose personal info: Sharing Social Security numbers, banking info, or tax documents opens the door to identity theft or financial fraud.
What To Do If You Interact With a Phishing Email
Think you may have clicked something suspicious? Here’s what to do:
Disconnect from the internet to stop any potential data transfer.
Change your passwords immediately, especially if you entered any login info.
Alert your IT or security team so they can run checks, isolate systems, and protect the rest of the network.
Monitor your bank and credit accounts for unusual activity.
Report the email (and don’t delete it!) so others don’t fall for the same scam.
How IT TechPros Protects Your Business
At IT TechPros, we understand the evolving landscape of cyber threats. Our comprehensive cybersecurity solutions are designed to provide robust protection and peace of mind:
24/7 Monitoring & Threat Detection: Continuous surveillance to identify and neutralize threats in real-time.
Incident Response Planning: Prepared strategies to swiftly address and mitigate security breaches.
Multi-Factor Authentication (MFA): Enhanced security layers to prevent unauthorized access.
Employee Training & Awareness: Regular sessions to educate your team on recognizing and avoiding phishing attempts.
Regular Security Audits: Proactive assessments to identify vulnerabilities and strengthen defenses.
Don't wait for a security breach to take action. Partner with IT TechPros to fortify your business against cyber threats. Contact us today to get started.